Database Monitoring Tools Comparison
Posted By admin On 02.06.20- Ms Sql Server Monitoring Tools
- Database Monitoring Sql Server
- Database Activity Monitoring Tools Comparison
- Sql Server Monitoring Tools
Buyer's Guide
- The business case for database security products
- Database security tool procurement
- The top database security products compared
- A who's who of the market-leading database security tool vendors
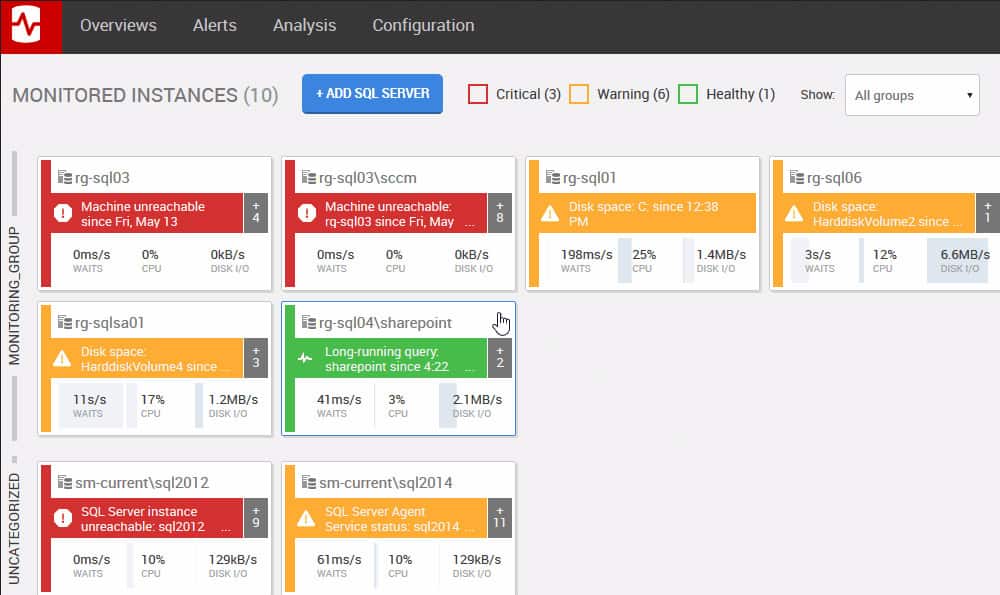
Rapidly resolve database performance issues – before they impact users. With more on your plate than ever – from massive data volumes and multiple database platforms, to DevOps and the cloud – database monitoring is more important than ever. You can’t afford any database downtime. So it’s easy to get caught up in fighting fires. Some of the ways in which database security tools do this. Compare Imperva Data Security (formerly SecureSphere for Data) Oracle Audit Vault and Database Firewall. According to the vendor, dbWatch is a complete and scalable database monitoring solution, helping enterprises monitor and manage any number of SQLServer. 29 rows The following tables compare general and technical information for a number of available.
BACKGROUND IMAGE: iSTOCK/GETTY IMAGES
The purpose of database security tools is to provide more complete protection of relational database management..
Continue Reading This Article
Enjoy this article as well as all of our content, including E-Guides, news, tips and more.
system offerings, beyond the security features that are integrated into those products. Some of these add-ons deliver high-end data, analysis and auditing tools as well. The appeal of database security tools is that they don't alter the database or application, and they result in only minimal performance impacts.
This article compares the strengths and weaknesses of several database security tools: database activity monitoring (DAM), database assessment and transparent database encryption products. The companies and products addressed in this article (shown in the following table) are all highly rated and leaders in the database security sector.
Fortinet FortiDB, IBM Guardium, Imperva SecureSphere and Vormetric Inc. are primarily appliance-driven products. The McAfee products (Database Activity Monitoring and Vulnerability Manager for Databases), HP Security Voltage, Protegrity USA Inc. and Trustwave DbProtect are primarily software-based products, and Oracle Advanced Security is an option with Oracle Database Enterprise Edition.
Features
The database activity monitoring products have similar feature sets: audit policy compliance (Payment Card Industry Data Security Standard, Health Insurance Portability and Accountability Act, Gramm-Leach-Bliley Act and so on), transaction blocking, separation of duties, centrally managed security, advanced reporting and more.
One differentiating factor is the underlying monitoring technology -- how the DAM gathers information -- which is typically via network monitoring, remote monitoring or local agents. Depending on a particular vendor's technology, the company might caution that SQL sniffing performed by network appliances or local agents offers limited visibility and can therefore miss some critical activity. Another may say that server input/output, network load and database performance is affected by agents needing to cache traffic to the local disk or send traffic over the network for analysis. In reality, today's agents are lightweight and typically impact performance by less than 5%, which is acceptable by industry standards. But there's no reliable way to compare the performance of various DAMs other than to test them in your own environment.
The types of supported databases is another factor to consider. Most DAM products can monitor Oracle, Microsoft SQL Server, IBM DB2, MySQL and Sybase, but some provide support for many more databases. Imperva SecureSphere adds IBM IMS, IBM Informix, IBM Netezza, MongoDB, PostgreSQL, Progress OpenEdge and Teradata to its list. However, vendors continually upgrade their products to be more inclusive and don't always have the most current information on their websites. So be sure to ask each vendor for a current list of supported databases.
Database assessment add-on tools check database configuration settings and patch levels to uncover vulnerabilities, and some integrate with DAM products for alerting and activity blocking. Assessment add-ons can be critical to database security because of the depth of inspection and reporting they offer, which is often lacking in database applications. Fortinet FortiDB, Trustwave DbProtect and Imperva SecureSphere include vulnerability management for databases, whereas IBM Guardium and McAfee sell it as a separate product.
For transparent database encryption, end-to-end protection, centralized policy management, scalability and minimal performance impact are important criteria. In this respect, Vormetric and HP Security Voltage shine. Both products are highly scalable and provide strong data encryption. Vormetric provides file system and volume encryption as well as access control. Voltage's>
Ease of deployment and use
Appliance-based products, by design, tend to be fairly easy to install. That said, the more complex products, such as IBM Guardium and Imperva SecureSphere, can take weeks to deploy and properly configure.
Fortinet FortiDB appliances, on the other hand, get high ratings for simple deployment and setup -- organizations can begin monitoring a database within an hour of unpacking the box. The main configuration steps involve specifying an IP address range, selecting the type of database server to monitor, choosing a port range, and entering a username and password. Auto discovery takes it from there.
For the software-based database activity monitoring and assessment products, the McAfee products setup is wizard-driven and very easy to configure. The Trustwave DbProtect dashboard, meanwhile, is crisp and well-organized, and the product provides great performance charts as well as operational and compliance reports.
Setting up transparent database encryption is a complex process. Vormetric, Voltage and Protegrity require installation and configuration of a management console and agents. Because Oracle Advanced Security is an option in Oracle Database Enterprise Edition, installation is minimal. However, transparent database encryption requires significant policy configuration and keystore setup. In this respect, Vormetric, Voltage and Protegrity make use of graphical user interfaces (GUIs), whereas Oracle configuration is performed at the command-line interface or through a GUI.
As for demo and evaluation units, all of the vendors let potential customers try an evaluation unit in their own environment. Fortinet and Vormetric also offer online demos. Regarding HP Security Voltage, organizations have to get in touch with a sales rep to request a demo -- unlike the other vendors, the option to request a demo isn't readily available from the HP website. Organizations can download a trial of McAfee Database Activity Monitoring and McAfee Vulnerability Manager for Databases for free.
Pricing
Database security tools pricing varies greatly, in both dollar amount and how the product is sold or licensed.
Regarding database monitoring and assessment products, Fortinet offers the most straightforward pricing. For example, Fortinet FortiDB appliances cost $15,000 to $37,000, and annual upgrade subscriptions and enhanced support add $3,700 to over $9,000 to the cost.
By contrast, Imperva SecureSphere Database Activity Monitoring is licensed by database transaction volume, so price varies based on the environment. With this model, a customer purchases only what's needed and can scale up or down as database activity monitoring needs change. The platform requires a virtual or hardware appliance and management server; the cost of a low-end hardware appliance alone starts around $30,000 and scales up to over $85,000 for higher-end units.
Some of the products, like McAfee Database Activity Monitoring and IBM Guardium, base pricing on the number of processor cores. In those cases, the companies prefer potential customers to contact the vendor or a reseller for specific pricing.
Pricing for transparent encryption is equally diverse. For example, Protegrity Database Protector is one of the highest priced products but is fairly clear-cut. Protegrity licenses its product for several different types of databases. The Protegrity Oracle Database Protector, for example, costs approximately $17,000 annually for a two-year license, or $45,000 for a perpetual license. And the management console -- Enterprise Security Administrator -- costs about $32,000 (two-year term) to $84,500 (perpetual) for a single environment.
In comparison, Oracle Advanced Security pricing is much more complex. The company sells Named User Plus agreements for smaller environments or Enterprise Edition per-core licenses for larger environments. Under a Named User Plus agreement, customers must purchase 25 licenses per processor, which cost $300 total, plus $66 for software updates, licensing and support. Enterprise Edition per-core licensing runs $15,000, plus $3,300 for software updates, licensing and support. Surprisingly, you can order Oracle Advanced Security licenses directly from the Oracle website.
Support
All of the companies offer standard support via phone, email or a customer portal, as well as free access to Web knowledge bases. Standard support is typically Monday through Friday during business hours with a four-hour response time. Premium support with 24x7x365 access and various levels of response time is available, typically at thousands of dollars per package.
Conclusions
Budget is often the primary criterion in any security product, but database security tools' purchasing metrics vary significantly. Deciding factors are whether an add-on product has all necessary required features, how it performs in an organization's environment, and how much effort is required to set up and maintain the product.
Ms Sql Server Monitoring Tools
Begin the vendor vetting process with a detailed list of features that your organization requires, then talk to vendor reps, get evaluation units or trial software, test the products in-house, and request accurate pricing for your particular environment. Then weigh the costs against completeness of feature set, ease of use and performance.
Fortinet and McAfee rank high on ease of use and cost for database monitoring and assessment, but they might not meet all of an organization's requirements. Regarding transparent database encryption, Vormetric, HP Secure Voltage and Protegrity edge out Oracle Advanced Security regarding ease of use and/or pricing simplicity.
Once an organization determines a short list of products, evaluate each vendor's longevity in the market. The database security sector has experienced a lot of churn over the last two to three years, with some companies making several strategic purchases and forming partnerships with cloud service providers, while others have been scooped up by the competition. It may be best to avoid vendors that are being acquired or are struggling to grow.
Next Steps
Be sure to check out the other features in this series: Part one is an introduction to database security tools for the enterprise. Part two defines four scenarios for deploying database security tools in the enterprise. Part three outlines nine steps you should take before purchasing database security products.
Learn the basics of database security tools in the enterprise
Here are the four enterprise scenarios for deploying database security tools
Ed Tittel asks:
Simply open Reflector Student and the device will pair to Reflector Teacher again automatically. It worked at one point, but useless now. Reflector 2 for windows. Mlaurel, UselessAfter having purchased reflector 2 and airparrot, I still can't get this app to connect. Developer Response,Hi. There’s no need to go through the pairing process again if you’re connecting to the same destination!View Connected ScreensReflector Student allows any paired student devices to view all of the screens connected to Reflector Teacher, including both teacher and student devices.
What types of database security tools does your enterprise use: database activity monitoring, database assessment, transparent database encryption or a combination of these?
- Modernize business-critical workloads with intelligence–DellEMC
- Digital Workspaces of the Future: Technology that Serves the People, Not Vice ..–Citrix
- Context-Aware Security Provides Next-Generation Protection–Citrix
The following tables compare general and technical information for a number of network monitoring systems. Please see the individual products' articles for further information.
- 1Features
Features[edit]
| Name | IP SLA Reports | Logical Grouping | Trending | Trend Prediction | Auto Discovery | Agentless | SNMP | Syslog | Plugins | Triggers / Alerts | MIB Compiler | WebApp | Distributed Monitoring | Inventory | Platform | Data Storage Method | License | Maps | Access Control | IPv6 | Latest release date | Latest release version |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Argus - The all seeing | Yes | Yes | Yes | No | No | Yes | Yes | Yes | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes | Unknown | Perl | Flat file, Berkeley DB | Artistic License | No | Yes | Yes | 2013-02 | 3.7 |
| Avaya VPFM | Yes | Yes | Yes | No | Yes | No | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Unknown | MySQL | Commercial | Yes | Yes | Yes | ||
| Cacti | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | PHP | RRDtool, MySQL | GNU GPL | Via plugin | Yes | Yes | 2019-06-07 | 1.2.4 |
| Check MK | Via plugin | Yes | Yes | Yes | Via plugin | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | C, Python | RRDtool | GNU GPL | Via plugin | Yes | Yes | 2019-02-17 | 1.5.0p12 |
| collectd | No | No | No | No | Push model; multicast possible | Yes | Yes | Yes | Yes | Yes | No | Viewing | Yes | No | C | RRDtool | GNU GPL | No | Apache ACL | Yes | 2018-10-24 | 5.8.1 |
| Cruz | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Java, C++, .NET | MySQL, Oracle | Commercial | Yes | Yes | Yes | 2019-02 | 8.0.0 |
| Entuity | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | C, C++, Java | MariaDB | Commercial | Yes | Yes | Yes | 2017-12-22 | 16.5 P3 |
| FreeNATS | Yes | Yes | No | No | Yes | No | No | Via plugin | Yes | In PHP Code | No | Full Control | No | No | PHP | MySQL | GNU GPL | No | Yes | Unknown | 2011-07-09 | 1.13.3b |
| Ganglia | No | Yes | Yes | No | Via gmond check in | No | Via plugin | No | Yes | No | No | Viewing | Yes | Unknown | C, PHP | RRDtool | BSD | Yes | No | Unknown | 2016-06-14 | 3.7.2 |
| Hinemos | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Java | PostgreSQL | GNU GPL | Yes | Yes | Yes | 2017-06-09 | 6.0.1 |
| HPE Openview Network Node Manager (NNMi) | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Via integration | Yes | Yes | No | Full Control | Yes | Yes | C++, Java, Perl | PostgreSQL, Oracle Database | Commercial | Yes | Yes | Yes | 2016-08 | 10.20 |
| Icinga | Via plugin | Yes | Yes | No | Via plugin | Yes | Via plugin | Via plugin | Yes | Yes | No | Full Control | Yes | Via plugin | C[1] | MySQL, PostgreSQL, Oracle Database | GNU GPL | Yes | Yes | 2019-03-19 | 2.10.4 | |
| InterMapper | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Viewing | Yes | Yes | Windows, Linux & Mac OS | PostgreSQL | Limited free, Commercial | Yes | Yes | Yes | 2017-07 | 6.1.5 |
| isyVmon | Yes | Yes | Yes | No | Via plugin | No | Yes | Yes | Yes | Yes | No | Full Control | Yes | Via plugin | PHP | RRDtool, MySQL | Limited free, Commercial | Via plugin | Yes | Yes | ||
| Kaseya Network Monitor | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Full Control | Yes | Yes | Unknown | FirebirdSQL | Commercial | Yes | Yes | Unknown | ||
| Munin | No | Yes | Yes | Yes | No | No | Yes | No | Yes | Partial | No | Viewing | Via nodes | Unknown | Perl | RRDtool | GNU GPL | Unknown | Unknown | Yes | 2016-09-19 | 2.0.26 |
| Nagios | Via plugin | Yes | Yes | No | Via plugin | Yes | Via plugin | Via plugin | Yes | Yes | No | Yes | Yes | Via plugin | C | Flat file, SQL (via ndoutils), MySql (Via Nconf) | GNU GPL | Yes | Yes | Yes[2] | 2019-07-29 | 4.4.4[3] |
| NeDi | No | Yes | Yes | No | Yes | Yes | Yes | Yes | No | Yes | No | Yes | Yes | Yes | Perl, PHP | Pg, MySQL, RRDTool, MariaDB | GPL3, Commercial | Yes | Yes | Yes | 2016-04 | 1.6[4] |
| Netdisco | No | No | No | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Perl | PostgreSQL | BSD | Yes | Yes | Yes | 2017-10 | 2.036011[5] |
| NeuralStar | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Unknown | MS SQL | Commercial | Yes | Yes | Yes | ||
| CA UIM fka Nimsoft Monitor | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes | Yes | Unknown | SQLServer, Oracle, MySQL | Limited free, Commercial | Yes | Yes | Yes | 2013-06-30 | 1.8.6 |
| Octopussy | No | Yes | Yes | No | Yes | Yes | No | Yes | Yes | Yes | No | Full control | No | Yes | Perl, ASP | MySQL | GNU GPL | No | Yes | No | 2017-06-03 | 1.0.16 |
| op5 Monitor | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Via plugin | C, PHP | Flat file, SQL | Limited free, Commercial | Yes | Yes | Yes | Monthly | 7.3.0 |
| OpenKBM | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Unknown | Proprietary with JDBC support | Commercial | Yes | Yes | Yes | ||
| OpenNMS | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Full Control | Yes | Yes | Java | JRobin / RRDTool / Apache Cassandra, PostgreSQL | AGPLv3 | Yes | Yes | Yes | 2018-01-13 | 21.0.3 |
| Opmantek NMIS | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Full Control | No | Yes | Yes | Yes | Perl | MongoDB, RRDtool | GPL, Commercial | Yes | Yes | Yes | 2015-10 | 8.5.10G |
| OPNET's AppResponse Xpert | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes | No | Unknown | Unknown | Commercial | Yes | Yes | Unknown | ||
| Opsview | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | No | Perl, C, ExtJS | SQL | Commercial | Yes | Yes | No | 2019-08-07 | 6.2 |
| OSI NetExpert | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Java, C++ | Oracle | Commercial | Yes | Yes | Yes | 2013-04 | 10.0 |
| PA Server Monitor | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | No | Viewing, Reporting | Yes | Yes | C++ | SQLite, Microsoft SQL Server | Commercial | Yes | Yes | No | 2014-07 | 5.5 |
| PacketTrap | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | No | Viewing, Reporting | Yes | Yes | Unknown | SQL | Commercial | Yes | Yes | Yes | ||
| Pandora FMS | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Perl, PHP, C++, JavaScript | MySQL, Oracle | GPLv2, Commercial | Yes | Yes | Yes | 2017-07 | 7.0 NG 707 |
| PathSolutions TotalView | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | No | Yes | Yes | Yes | Windows | SQLite | Commercial | Yes | Yes | No | 2018-06-01 | 9.01 |
| Performance Co-Pilot | No | Yes | Yes | No | Yes | Optional, Limited | Yes | Yes | Yes | Yes | No | Viewing | Yes | Yes | CPerl, Python, POSIX, MinGW | Flat file | GPL, LGPL | No | Yes | Yes | 2016-11-15 | 3.11.6 |
| PRTG | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Windows | Flat file | Limited free, Commercial | Yes | Yes | Yes | 2019-05-15 | 19.2.50 |
| ScienceLogic | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Python | MySQL | Commercial | Yes | Yes | Yes | ||
| SevOne | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | C, C++, PHP | MySQL | Commercial | Yes | Yes | Yes | 2018-09 | 5.7.2.4[6] |
| Shinken | Via plugin | Yes | Yes | No | Yes | Yes | Via plugin | Via plugin | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes | Via plugin | Python | Flat file, MySQL, Oracle, Graphite, Sqlite, MongoDB | AGPL | Yes | Yes | Yes | 2016-03-10 | 2.4.3 |
| Solarwinds | Yes | Yes | Yes | Yes | Yes | Partial | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | .NET | SQL | Commercial | Yes | Yes | Yes | ||
| Spiceworks | ? | Yes | ? | ? | Yes | Yes | ? | ? | Yes | Yes | ? | ? | ? | Yes | PHP | Sqlite | ? | Yes | ? | ? | 2018-03-21 | 7.5.00107 |
| CA Spectrum | Yes | Yes | Perf. AddOn | Perf. AddOn | Yes | No | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | C++, JavaScript | Sleepycat-QSL, MySQL | Commercial, per Device | Yes | Yes | Yes | 2018-03 | 10.2 |
| Xymon/Hobbit | Yes | Yes | Yes | No | Via plugin | Via plugin | Via plugin | No | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes | Via plugin | C, Shell | Flat file, RRDTool, MySQL via plugin | GNU GPL | Via plugin | Apache ACL | No | 2017-01-18 | 4.3.28 |
| Vigilo NMS | Yes (NMS and NOC editions) | Yes | Yes | Yes via integration | Yes via integration | Yes | Yes | Yes via Prelude SIEM | Yes | Yes | No | Viewing, Acknowledging, Reporting | Yes (NMS and NOC editions) | Yes via GLPI | Python, Perl | PostgreSQL, RRDtool | Free (GPLv2) OSS edition, Commercial NOC/NMS editions | Yes (NMS and NOC editions) | Yes (NMS and NOC editions) | Via plugin | 2017-09-14 | 4.1.0 |
| Zabbix | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | C, PHP | Oracle, MySQL, PostgreSQL, IBM DB2, SQLite | GNU GPL | Yes | Yes | Yes | 2019-03-29 | 4.2 |
| Zenoss Core | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Full Control | Yes | Yes | Python, Java | ZODB, MariaDB, Apache HBase | Free Core GPL, Commercial Enterprise | Yes | Yes | Yes | 2018-01-09 | 6.1.0 |
| Name | IP SLA Reports | Logical Grouping | Trending | Trend Prediction | Auto Discovery | Agentless | SNMP | Syslog | Plugins | Triggers / Alerts | MIB Compiler | WebApp | Distributed Monitoring | Inventory | Platform | Data Storage Method | License | Maps | Access Control | IPv6 | Latest release date | Latest release version |
Legend[edit]

Database Monitoring Sql Server
Database Activity Monitoring Tools Comparison
Sql Server Monitoring Tools
- No: There is no web-based frontend for this software.
- Viewing: Network data can be viewed in a graphical web-based frontend.
- Acknowledging: Users can interact with the software through the web-based frontend to acknowledge alarms or manipulate other notifications.
- Reporting: Specific reports on network data can be configured by the user and executed through the web-based frontend.
- Full Control: ALL aspects of the product can be controlled through the web-based frontend, including low-level maintenance tasks such as software configuration and upgrades.
- Distributed Monitoring
- Able to leverage more than one server to distribute the load of network monitoring.
- Inventory
- Keeps a record of hardware and/or software inventory for the hosts and devices it monitors.
- Platform
- The platform (Coding Language) on which the tool was developed/written.
- Data Storage Method
- Main method used to store the network data it monitors.
- License
- License released under (e.g. GPL, BSD license, etc.).
- Maps
- Features graphical network maps that represent the hosts and devices it monitors, and the links between them.
- Access Control
- Features user-level security, allowing an administrator to prevent access to certain parts of the product on a per-user or per-role basis.
- IPv6
- Supports monitoring IPv6 hosts and/or devices, receiving IPv6 data, and running on an IPv6-enabled server. Supports communication using IPv6 to the SNMP agent via an IPv6 address.
See also[edit]
References[edit]
- ^https://wiki.icinga.org/display/icinga2/Intro
- ^'NRPE IPv6 Support'.
- ^'Nagios Core Changelog'. Retrieved 2019-07-29.
- ^'NeDi Find It!'. Retrieved 2016-10-07.
- ^'Welcome to Netdisco!'. Retrieved 2018-09-06.
- ^'What's New in 5.6 - SevOne'.
